VaultIC292
The VaultIC292 is a ready-to-use secure microcontroller designed to bring a robust, unique digital identity to a device, essential for applications such as creating a secure connection to a cloud or a local network using TLS, authenticating a USB-C device or a QI Wireless charger.
Tamper Resistant
Tamper resistant proven hardware platform that is used to secure sensitive applications like National ID cards, e‑Passports, Bank, Pay-TV Access Control cards and IoT.
Easy Integration
Enable state-of-the-art security in an easy and cost effective way: VaultIC292 delivers all the required cryptography and keys in a ready-to-use module.
Pre-Provisioned
Ideal for zero-trust environment as it can be pre-provisioned with a unique digital identity and birth certificate in our secure production facilities.
Small Footprint
VaultIC292 helps optimize your PCB size with its small package, reduced number of connections and limited number of external components.
Protocol Ready
VaultIC292 can be pre-configured with private keys & X509 Certificates compliant with protocols such as Matter, Wi-SUN or OPC, for seamless authentication


Cloud Ready
VaultIC292 can be pre-configured with private keys & X509 Certificates to be used for AWS and Azure Cloud commissioning


Block Diagram VaultIC292
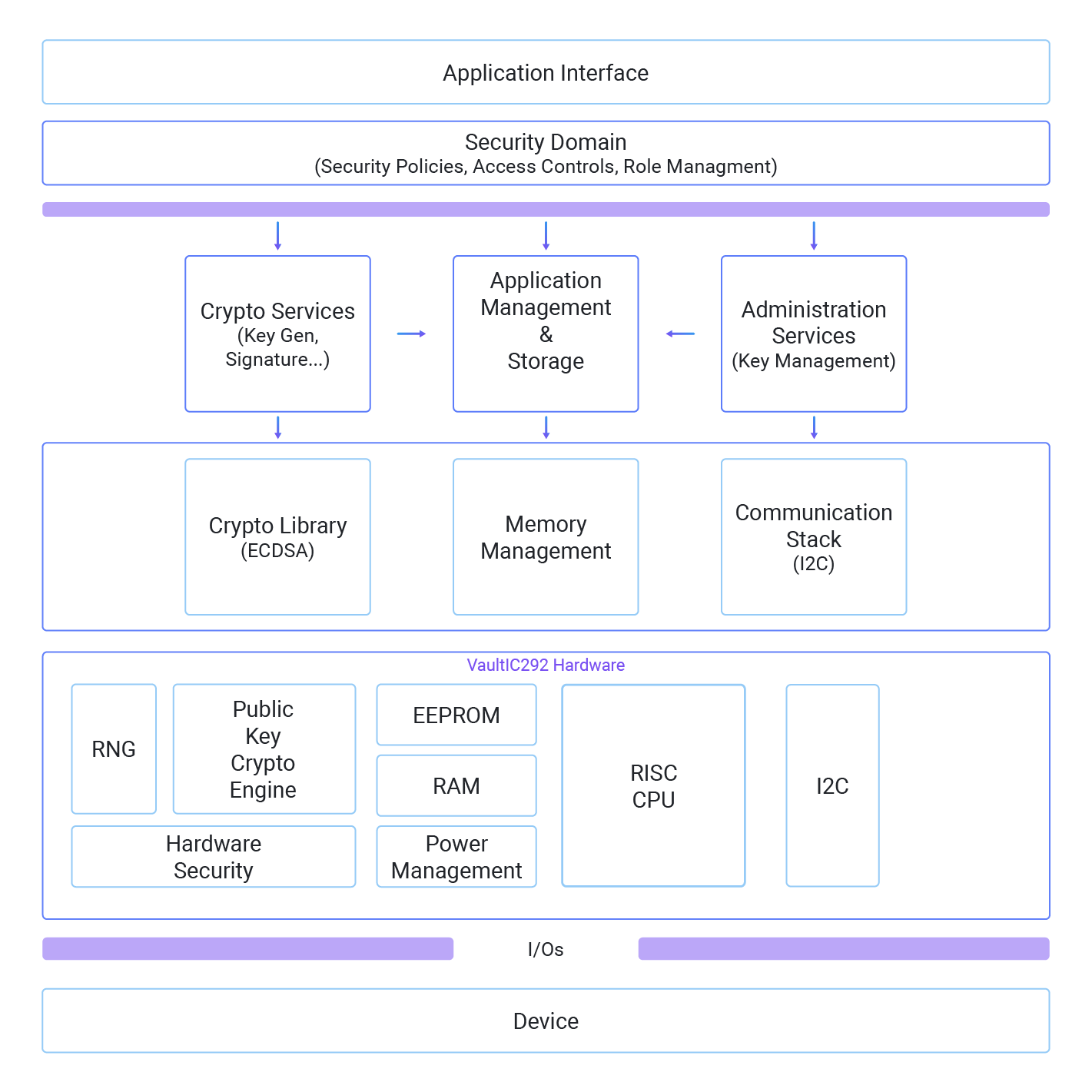
Technical Features
- Key pair generation
- Digital signature (ECDSA) P-256
- Shared secret generation (ECDH)
- True Random Number Generation
- Stores up to 5 static key pairs and 3 ephemeral key pairs
- Hardware: CCEAL5+ ready
- True RNG: NIST SP 800-90A, NIST SP 800-90B
- ECDSA: FIPS 186-4
- ECC Parameters: NIST SP 800-186
-
Hardware 16-bit Public Key Crypto Accelerator
-
Power consumption: 64µA in standby mode and 3 to 5mA during CPU-intensive operations
-
Operating temperature : -40°C to +105°C
-
Operating range: 1.62V to 5.5V
-
I²C
-
UDFN-8 (RoHS compliant) 2mm x 3mm
-
DFN-6 (RoHS compliant) 2mm x 3mm
They trust us



.png)
Recommended Applications

INeS PKI-SaaS platform for managing the DAC for Matter
This paper addresses a complex fundamental component of securing IoT: how to give devices and services secure identities so they can interact securely.





